Hack Router Port 53 Tcp
One of the goals of taking over the router is to get control of the Domain NameSystem on the router, so an attacker can reroute traffic of certain sites to hisown site (a so called 'man in the middle' attack). There are a few possible wayshow this could be done, where UPnP can be used as part of the hack. Please notethat the methods described here are possible ways to get access to DNS, but Ihave not actually got them to work, or have not found the time to work on it,like in the case of making a customized firmware.
- Step by Step How to Randomly Hack a Home Routers. We should select an IP range. I have selected IP range that includes my public IP address. Now let's scan for home routers. When you finished your scan, You can find IP addresses which has open ports such as http port(80), ftp port(21) and telnet port(23).
- Well both of the hacking has the same process. Let’s summarize what we must do. Confirm the website or a computer you want to hack. Find or trace their IP address. Make sure that IP address is online Scan for open ports Check for vulnerable ports ( enumerate the services running on ports and try.
Me bei impatient, I wanted to check if my Kali Linux was actually doing anything to ADSL router hack. I used following command in a separate Terminal to monitor what my PC was doing it was doing a lot tcpdump -ni eth0 That’s a lot of connected hosts with TCP Port 80 open. Some got ‘tcpwrapped’ marked on them.
Hack Router Port 53 Tcp Login
Accessing DNS from the outside
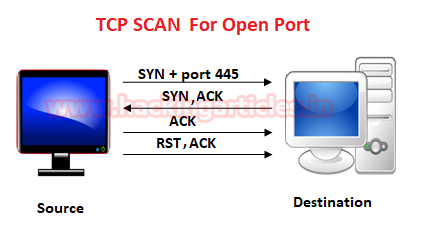
Hack Port 53
Many routers allow port 53 (UDP and TCP) on the WAN port the router to beportmapped to port 53 (UDP and TCP) on the inside of the router itself,exposing the DNS on the router to the outside world. The DNS servers on mostrouters seem to be pure forwarders though, with no caching.
Uploading new firmware
While not directly because of UPnP, but if you can get the adminstrativeinterface access on the outside with a UPnP port forward and the defaultpassword is still on, you could upload a new firmware, that is nearly exactlythe same, except for DNS.
To properly recreate a firmware you need tohave good knowledge about how the firmware on the device is constructed,compile a few new executables, use the right offsets in the firmware and hopethat the device will accept it and it will not be bricked and no one detectsthat the device has been tampered with. For crackers this is currently tooexpensive to do, but it is certainly the most effective way.